Table of Contents
What is K3s?
K3s (https://k3s.io/) is a Kubernetes solution created by Rancher Labs (https://rancher.com/) that promises easy installation, few requirements and minimal memory usage.
For the approach of a Demo/Development environment this becomes a great improvement on what we have talked about previously at Kubernetes: Create a minimal environment for demos , where we can see that the creation of the Kubernetes environment is complex and requires too many resources even if Ansible is the one who performs the difficult work.
We will see if what is presented to us is true and if we can include the Metallb tools that will allow us to emulate the power of the Cloud providers balancers and K8dash environments that will allow us to track the infrastructure status.
K3s Download
We configure the virtual machines in the same way as for Kubernetes, with the installation of dependencies:
#Debian
sudo apt-get install -y ebtables ethtool socat libseccomp2 conntrack ipvsadm
#Centos
sudo yum install -y ebtables ethtool socat libseccomp conntrack-tools ipvsadmWe download the latest version of k3s from https://github.com/rancher/k3s/releases/latest/download/k3s and put it in /usr/bin with execution permissions. We must do it in all the nodes.
What is K3s?
K3s includes three “extra” services that will change the initial approach we use for Kubernetes, the first is Flannel, integrated into K3s will make the entire layer of internal network management of Kubernetes, although it is not as complete in features as Weave (for example multicast support) it complies with being compatible with Metallb. A very complete comparison of Kubernetes network providers can be seen at https://rancher.com/blog/2019/2019-03-21-comparing-kubernetes-cni-providers-flannel-calico-canal-and-weave/ .
The second service is Traefik that performs input functions from outside the Kubernetes cluster, it is a powerful reverse proxy/balancer with multiple features that will perform at the Network Layer 7, running behind Metallb that will perform the functions of network layer 3 as balancer.
The last “extra” service of K3s is servicelb, which allows us to have an application load balancer, the problem with this service is that it works in layer 3 and this is the same layer where metallb work, so we cannot install it.
K3s Master Install
On the first node (which will be the master) to be installed, we execute /usr/bin/k3s server --no-deploy servicelb --bind-address IP_MACHINE, if we want the execution to be carried out every time the machine starts we need to create a service file /etc/systemd/system/k3smaster.service
[Unit]
Description=k3s
[Service]
ExecStart=/usr/bin/k3s server --no-deploy servicelb --bind-address 192.168.8.10
Restart=always
StartLimitInterval=0
RestartSec=10
[Install]
WantedBy=multi-user.targetAnd then, we execute
sudo systemctl enable k3smaster
sudo systemctl start k3smasterTo launch K3s and install the master node, at the end of the installation (about 20 seconds), we will save the contents of the file /var/lib/rancher/k3s/server/node-token since it is the activation code for the nodes (token), it is important to see that teh token is base64 and to use it you have to decode it.
Configure Metallb
Before preparing the nodes we proceed to install Metallb and the K8dash panel:
$ sudo mkdir ~/.kube
$ sudo cp -i /etc/rancher/k3s/k3s.yaml $HOME/.kube/config
$ sudo k3s kubectl apply -f "https://raw.githubusercontent.com/danderson/metallb/master/manifests/metallb.yaml"
$ sudo k3s kubectl apply -f "https://raw.githubusercontent.com/herbrandson/k8dash/master/kubernetes-k8dash.yaml"We must note that to minimize space, kubectl is included within the k3s executable itself, which makes it ideal for environments with very little storage space.
To activate Metallb we create a configuration that will have the content:
apiVersion: v1
kind: ConfigMap
metadata:
namespace: metallb-system
name: config
data:
config: |
address-pools:
- name: my-ip-space
protocol: layer2
addresses:
- 192.168.8.240/28That when applying with k3s, kubectl apply -f pool.yml will configure Metallb so that any service with loadBalancer obtain one IPs defined in the specified range, in our example the range corresponds to the network defined in inventory.k3s.yml and is between xxx240 to xxx254.
apiVersion: v1
kind: Service
metadata:
name: k8dashlb
namespace: kube-system
spec:
ports:
- name: http
port: 80
protocol: TCP
targetPort: 4654
selector:
k8s-app: k8dash
type: LoadBalancerTo test this we load a service to access K8dash:
apiVersion: v1
kind: Service
metadata:
name: k8dashlb
namespace: kube-system
spec:
ports:
- name: http
port: 80
protocol: TCP
targetPort: 4654
selector:
k8s-app: k8dash
type: LoadBalancerWe apply with k3s kubectl apply -f service.yml and we will see which IPs have the active services with:
$sudo k3s kubectl get services -A
NAMESPACE NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
default kubernetes ClusterIP 10.43.0.1 <none> 443/TCP 32m
kube-system k8dash ClusterIP 10.43.183.3 <none> 80/TCP 31m
kube-system k8dashlb LoadBalancer 10.43.86.34 192.168.8.240 80:32324/TCP 31m
kube-system kube-dns ClusterIP 10.43.0.10 <none> 53/UDP,53/TCP,9153/TCP 32m
kube-system traefik LoadBalancer 10.43.91.178 192.168.8.241 80:30668/TCP,443:31859/TCP 30mWe see on the one hand that the services marked as loadBalancer have correctly taken the IPs, both has beed configured, the Traefik service deployed by K3s and the K8dashlb.
Install K3s Nodes
In the rest of the nodes we execute /usr/bin/k3s agent --server https://IP_MASTER:6443 –token DECODED _BASE64_TOKEN, if we want the execution to be every time the machine starts we need to configure a service creating the file /etc/systemd/system/k3s.service
[Unit]
Description=k3s
[Service]
ExecStart=/usr/bin/k3s agent --server https://IP_MASTER:6443 --token TOKEN_DECODIFICADO_BASE64
Restart=always
StartLimitInterval=0
RestartSec=10
[Install]
WantedBy=multi-user.targetAnd we run to configure the service
sudo systemctl enable k3s
sudo systemctl start k3sConclusions
If we access to the service IP for K8dashlb service obtained previously and with the token obtained with k3s kubectl get secret `k3s kubectl get secret|grep ^k8dash|awk '{print $1}'` -o jsonpath="{.data.token}"|base64 -d (note: in Ansible deployment must be returned the IP and the token to access). We can check then the operations in the platform: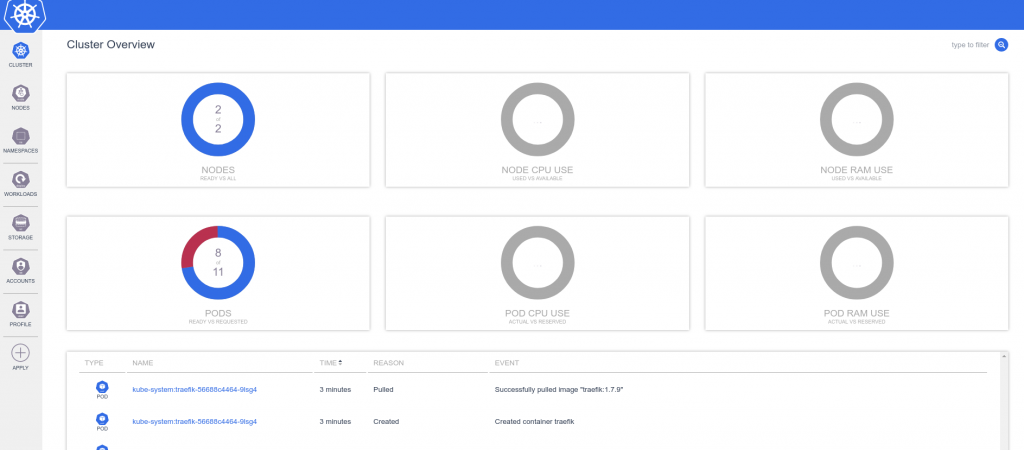
Finally a small comparison between kubernetes and k3s in memory use, both fresh installed:
- Kubernetes master: 574 MB
- Kubernetes node: 262 MB
- K3s master: 260 MB
- K3s node: 137 MB